How SamSam Ransomware works in a nutshell
SamSam is ransomware that 'spies' for a long time after its initial infection, without being detected. SamSam uses vulnerabilities to attack specific organisations. The creators of the ransomware ask for ransom after SamSam removes or makes it impossible for the victim to access his own data.
Organisations that deal with SamSam mainly consist of businesses where there is a great chance of receiving an amount of money in exchange for recovering the data, such as hospitals and educational institutions.
SamSam uses vulnerabilities to gain access to a victim's network by executing brute-force tactics against weak passwords, including the Remote Desktop Protocol (RDP). SamSam ransomware is a modified infection that is used in targeted attacks, often used with a wide range of exploits or brute-force tactics. Based on run-ins with the infection, it was determined that attacks on targets occurred via vulnerable JBoss host servers during a previous wave of SamSam attacks in 2016 and 2017. In recent months, several Dutch companies have been affected by this relatively new form of Ransomware.
SamSam Ransomware strikes again in 2018
In 2018 SamSam utilised vulnerabilities in RDP systems (Remote Desktop Protocols), Java-based web servers or FTP (File Transfer Protocol) servers or used brute-force attacks against weak passwords to access networks. From here the makers of the ransomware start with activities that could have destructive consequences.
The makers have so far earned hundreds of thousands of dollars in the form of ransom, paid in bitcoin.
SamSam is not new. It first appeared in 2016 but attracted the attention of the IT Security community again regularly. The developers of this 'hostage' software put great efforts into covering up their traces. In many cases, the initial infection vector of the attacks is not clear or some steps of the attack chain are missing. The attackers try to make the analysis of its original source more difficult by removing files involved in an attack, including the load itself, and by changing the deployment methodology used.
Dutch companies have been hit by a new form of this ransomware software in recent months called SamSam. It's unknown how much financial damage the software has caused yet.
How does SamSam ransomware work?
SamSam works in another way than previous ransomware such as WannaCry and GandCrab. These types of ransomware hit directly after infection, locked files and then demanded ransom. The creators of SamSam though wait and wait to monitor network and/or user activities for a longer period of time. The creators analyse where they have penetrated the network and whether they can penetrate even deeper into systems. This is done to cause as much damage as possible and to make data unreachable.
SamSam then silently removes or sabotages the backups to prevent a company from undoing the contamination. As soon as this has happened, SamSam strikes and the files will be locked. A well-known solution that can detect SamSam Ransomware was developed by CrowdStrike. For a technical deep-dive explanation about SamSam, read the CrowdStrike blog with an in-depth analysis of SamSam ransomware and boss spider.
Samsam ransomware detection: CrowdStrike Falcon Prevent
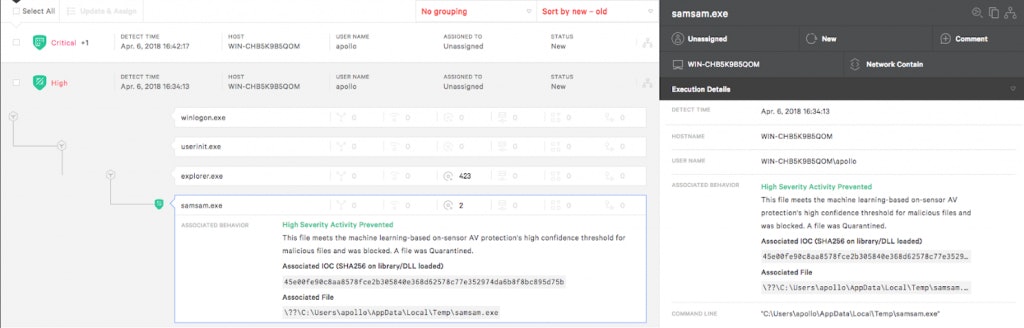
SamSam is unique in terms of how it is delivered to a system. Collecting user credentials to generate unique RSA public keys ensures that an organisation must pay for each infected user to decrypt the files. In addition, it uses cleanup files for standalone executable files. Combined with the fact that other variants are fully executed in its memory, it is extremely difficult to forensically collect the payload from the disk or memory. Despite these challenges, Falcon Prevent next-gen Anti-Virus can detect and prevent the malware even before the file encryption can be performed as shown below:
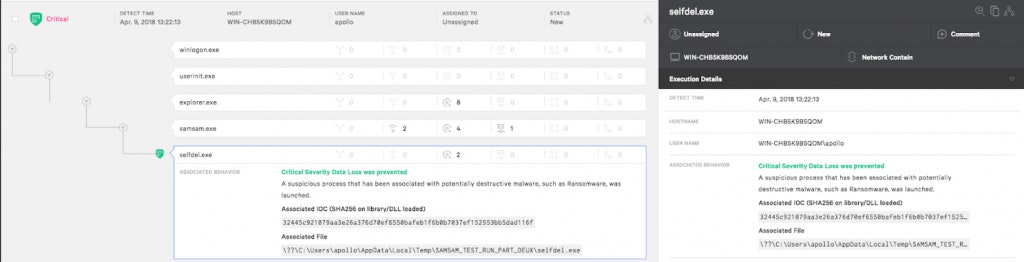
Falcon Prevent can also detect the selfdel.exe file and prevent it from running once it is loaded by the payload, as shown below:
These prevention methods are based on the behavioural patterns on a network as shown by Samsam in combination with the Machine Learning Algorithm of CrowdStrike.
Suspected creators of SamSam indicted
Two men from Iran have already been indicted in the United States because they had been involved in creating and distributing the SamSam ransomware since 2015. Both men are fugitives.
In the US, at least two hundred organisations have been hit by SamSam, including the Atlanta and Newark municipalities, the San Diego port and at least three hospitals. The two suspects would have earned millions.
The Washington Treasury has blacklisted two other Iranians because they would have laundered the ransom.
SamSam: Successor to Petya and WannaCry
SamSam is not the first software that hijacks systems and then demands a ransom. WannaCry (May 2017), Petya (June 2017), BAD RABBIT (October 2017) and GANDCRAB (January 2018) were already well-known ransomware before SamSam was known.
Our team is ready for you
Do you want to know more about this topic? Leave a message or your number and we'll call you back. We are looking forward to helping you further.